|
Greetings from the Hoplite Lab!
At Hoplite, we're constantly working to solve security problems large, and small. Every step of the way we look for opportunities to build foundational components that will enjoy heavy re-use, in fact, we actively avoid one-trick code ponies. The goal of this blog series is to share some early insight into the projects and prototypes that will be coming to life in 2017. For this first post in the series, we'll be covering a much-maligned topic, Technical Support Scams, and how we're working to interrupt these scams using Threat Intelligence. Here's a bit of background to get things started: Scam Infrastructure – Technical Support scammers will typically have a few pieces of infrastructure in place to support their criminal activities:
The Scam – The criminals behind Technical Support scams tend to focus on impersonating support staff of well-known tech companies, Microsoft, HP, Dell, and others to maximize their target market (of victims). The scam typically begins with a victim seeing a malicious ad (popup or otherwise) that indicates their machine has been compromised, but offering a lifeline in the form of a technical support number to call. Typically, if the victims are convinced the malicious ad was legitimate, they need little urging to call the criminals immediately to get the problem resolved. Once the victim contacts the scammers via telephone, the hustle is on. The scammers will typically, and with practiced skill we might add, lead the victim through a process to 'prove' the compromise reported by the false malicious ad or popup. Once the victim has been 'hooked', the scammer will provide clear instructions for the victim to download and install remote access software from the scammer's 'company' website. Once the remote access software is installed, the scammer will collect the victim's contact and credit card information before proceeding with fixing the purported system compromise. The Impact – Beyond the invasion of privacy, and common ongoing theft of private, and financial data, the one-time fees charged by the Technical Support scammers can range up to $500 US, but the impact typically doesn't stop there. Annual 'support' contracts or follow-up support calls offered by the scammers can cost victims hundreds or thousands more. Solution from the Lab – If you're in IT and reading this, you probably spotted several areas where the scam could have been interrupted with technology. If victims, or more importantly their computers, had access to relevant information indicating the original scammer ads, websites, or even telephone numbers (more on this topic soon), were malicious, the scams could be stopped cold (just like your anti-virus package identifying known malware). Enter Hoplite Threat Intelligence On any given day, the Hoplite Threat Intelligence Platform identifies over 1.5 Million unique network (IP, domain and URL) threat indicators. With Technical Support scams becoming commonplace, the Hoplite team has set about enhancing our Threat Intel Platform to automatically identify and track infrastructure being used by scammers all over the world. By identifying and tracking the domains and URLs being used by scammers to distribute malicious ads, remote access software and other malware, Hoplite solutions, and that of our Technology Partners, can automatically interrupt Technical Support and other scams. Blocking access to install remote access software or malware on a victim's computer makes the scammer just a voice on the phone, a much easier problem to solve J To this end, we're happy to announce the release of over 10,000 Technical Support Scam domains and URLs into a new channel of our Threat Intelligence Platform. These new indicators will be refreshed and refined automatically by our collection of diligent bots, with occasional input from human analysts (automation is king at Hoplite). Active Network Defense (AND), HopliteDNS Commercial, and Threat Intel API subscribers will automatically gain the benefit of this new Threat Intelligence. Other Recommendations Patch Your Software – Keeping your software updated can help to avoid over 80% of existing vulnerabilities. Privacy-enhancing Browser Extensions – Installing browser extensions like the EFF's 'Privacy Badger' and 'NoScript' that help to reduce privacy violating ad-trackers and popups can also help to reduce the possibility that you'll even see the scammer's ad content. HoplieDNS – Is a simple, effective layer of protection for any network. HopliteDNS leverages Hoplite Threat Intelligence to block access to existing and emerging threats without additional hardware or software. Sign-up Here: http://dns-preview.hoplite.io
0 Comments
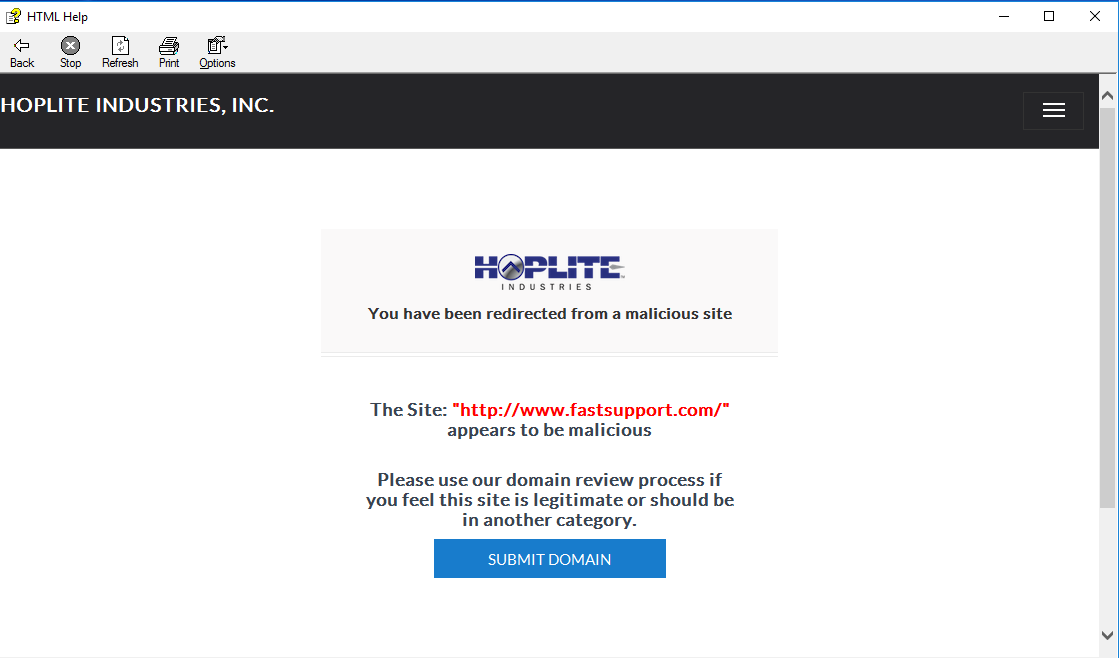
Another bad security outcome avoided by HopliteDNS, see the screenshot below, taken from a 'Microsoft Tech Support' scam attempt. We continue to see benefits of taking a Threat Intel-first approach to DNS, unlike the content filtering approaches (couched as security) taken by the industry giants. Join us and make DNS an instant, effective part of your organizational security. http://dns-preview.hoplite.io/
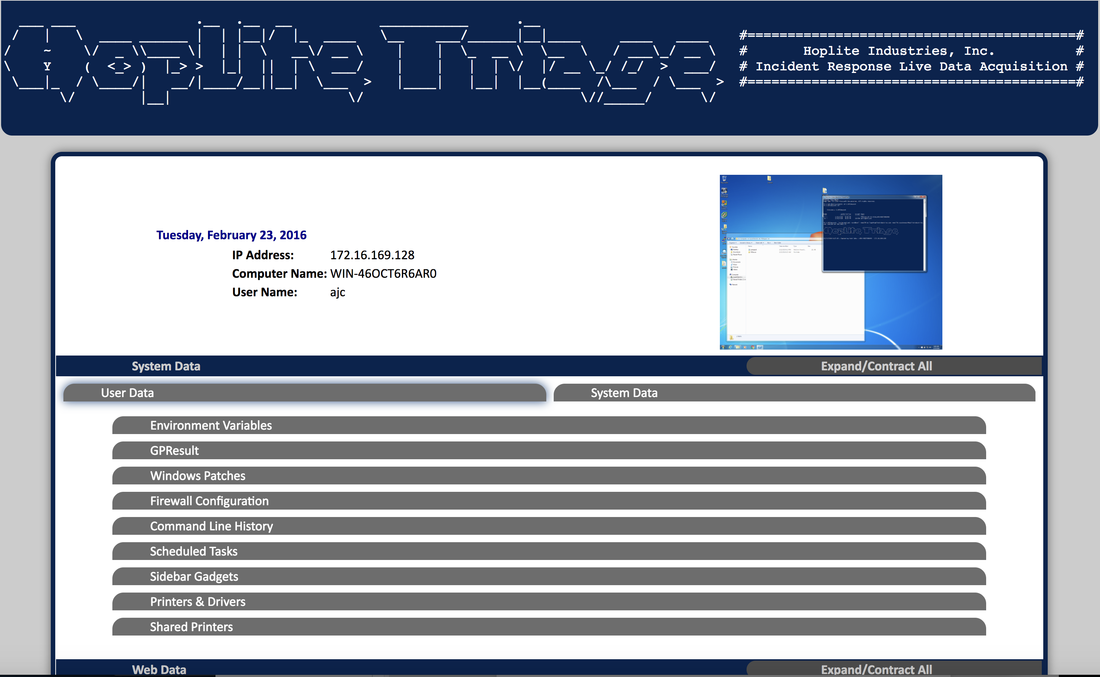
Hello! We wanted to share some background on 'PSInspect', a useful open source Incident Response (IR) tool that we maintain at Hoplite. PSInspect is a pre-imaging, first-response tool for suspect/compromised Windows (Vista/Server 2013 and later) systems, that quickly gathers hundreds of often fleeting pieces of OS and filesystem metadata. PSInspect is written in PowerShell with no external dependencies, making it a perfect tool for IT, InfoSec and DFIR professionals to keep in their go-bags and toolkits. PSInspect can be run locally or over a network and produces a comprehensive single-file report that is easy to share and to leverage for incident reporting and investigations. PSInspect is being used in Banking/Finance, Education, Healthcare and Fortune 1000 environments. Feel free to take a moment to check it out and make it part of your toolkit today: https://github.com/hl-repos/PSInspect PSInspect is one of several Hoplite IR tools, in the near future we'll share some information on 'LiveIR', the cloud-based big brother to PSInspect.
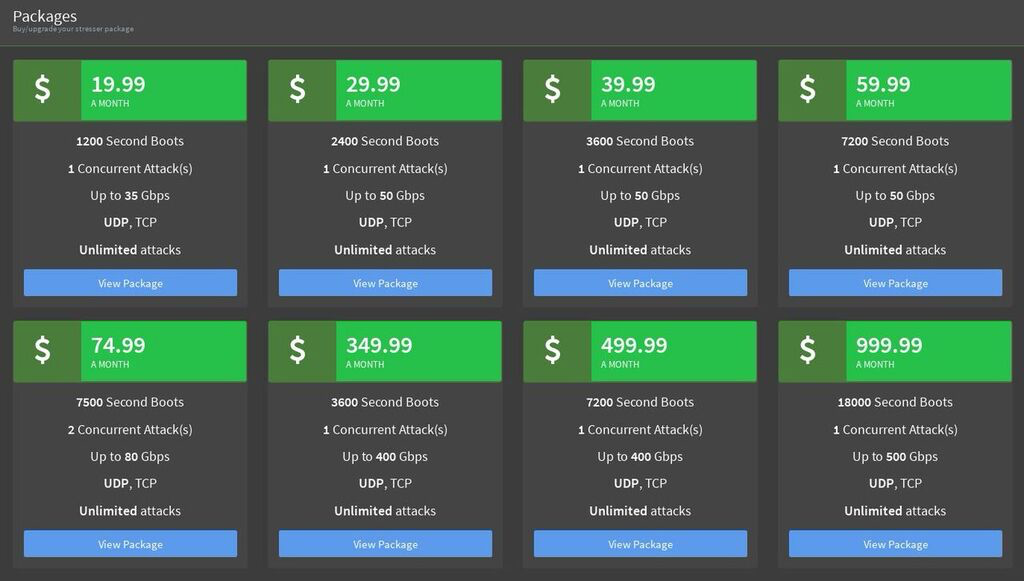
The Cost of Cyber Offense Versus Defense If you weren't already aware, adversaries cyber criminals have a thriving market that delivers all manner of malware, ransomware, DDoS and many other forms of Malevolence-as-a-Service. The image below was scraped from a darkweb retail front selling 'booter' or 'stresser' DDoS-as-a-Service, just one of dozens active at this moment. Unlimited 500Gbps+ attacks for less than $1,000/month, MUCH less expensive and complex than maintaining corresponding defenses.
I'm not sharing this to advertise for the bad guys, but rather to beg two questions: 1. Does it make sense to continue 'Doing What We've Always Done' when an adversary has clear asymmetric advantages (cheap, readily accessible and effective weapons)? 2. Does it make sense to grant your adversaries freedom of action to always bring attacks and conflict to your doorstep (the edge of your network)? The short answer to both is clearly 'No'. I encourage you to start the week by looking at InfoSec from a different angle, join us at Hoplite in gaining insights into relevant threats before they occur, move the fight from your doorstep and change adversary economy to your advantage. https://hoplite.io |
AuthorHoplite Team ArchivesCategories |

 RSS Feed
RSS Feed